We prioritize the security and privacy of patient health data through our robust End-to-End Encryption (E2EE) feature. E2EE ensures that patient information remains secure throughout its lifecycle within the app, offering unparalleled protection against unauthorized access and breaches.
Understanding End-to-End Encryption (E2EE):
End-to-End Encryption (E2EE) is a security measure that encrypts data at the source and decrypts it only at its intended destination. This means that data is encrypted on the user’s device (client-side) and can only be decrypted by the recipient (server-side), ensuring that even the service provider (TINA app) cannot access the plaintext data.
Why Use End-to-End Encryption?
E2EE is crucial for safeguarding sensitive patient health data:
- Enhanced Security: By encrypting data both in transit and at rest, E2EE prevents unauthorized parties, including hackers and malicious actors, from accessing or intercepting patient information.
- Privacy Protection: It ensures patient confidentiality by ensuring that only authorized personnel with the decryption key can access the data, even if intercepted during transmission or stored on servers.
Benefits of End-to-End Encryption (E2EE):
Implementing E2EE in TINA app offers several benefits:
- Advanced Security Measures: Protects patient health data from unauthorized access and breaches.
- Compliance: Helps healthcare organizations comply with strict data protection regulations, such as HIPAA, GDPR, and others.
- Trust and Confidence: Builds trust with patients and stakeholders by demonstrating a commitment to data security and privacy.
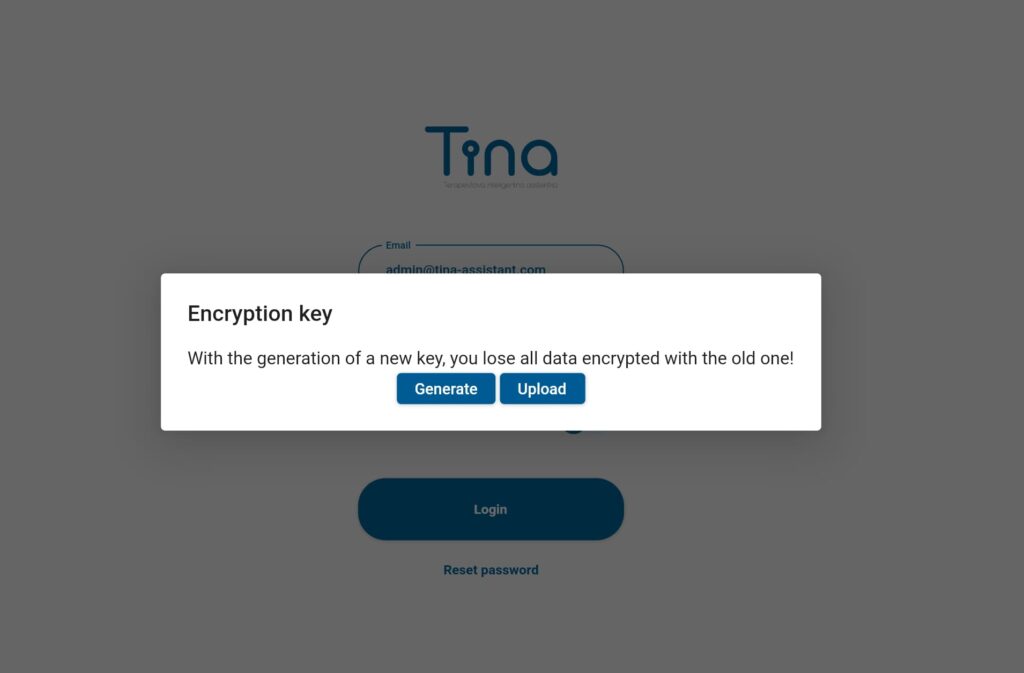
Setting Up End-to-End Encryption (E2EE) in TINA:
Step 1: Admin Login and E2EE Key Setup
When the admin of an organization logs in for the first time, they will receive a popup notification to either generate a new E2EE key or upload an existing one.
Step 2: Generating a New E2EE Key
If choosing to generate a new key, the TINA system will provide a file containing the encryption key. This file must be securely stored by the admin to ensure ongoing access to encrypted data. The admin will also have to provide this key to every user so they can log into the organisation.
Step 3: Key Usage for Security
The E2EE key must be used each time TINA is accessed from a new browser or device. This ensures that encrypted data remains protected and accessible only to authorized users.
Step 4: Caution with Key Management
It is crucial to exercise caution with the E2EE key. Losing the key can result in permanent loss of access to encrypted data, as decryption without the key is extremely challenging.
Additional Security Measures:
- Regular Backups: Maintain secure backups of the E2EE key to prevent loss or corruption.
- Training and Awareness: Educate staff about the importance of E2EE and secure key management practices to minimize risks.
Troubleshooting Tips:
Encountering issues with E2EE setup? Here’s how to address common concerns:
- Key Loss: If the E2EE key is lost, contact TINA support immediately for assistance in recovery or re-establishment of encryption.
By implementing End-to-End Encryption (E2EE) in TINA, you can significantly enhance the security and privacy of patient health data. Protect sensitive information effectively, comply with regulatory requirements, and build trust with patients and stakeholders. For further guidance or support, please reach out to our dedicated customer support team. We’re committed to ensuring your data remains secure and your practice runs smoothly with TINA.